Cybersecurity for Beginners: Common Types of Cyber Threats and Cybar Attacks Explained
Most individuals and businesses have found ways to counter cyber attacks, using a variety of security measures and their common sense. Today's post is all about cybersecurity threats and how to prevent them. We're going to examine eight of the most common cybersecurity threats that your business could face and the ways to avoid them. Just as a pollution was a side effect of the Industrial Revolution, so are the many cybersecurity vulnerabilities that come with the increased internet connectivity. Cyber attacks are exploitations of those vulnerabilities.
So before we actually jump into the session let me give you how the session will actually work. We are going to discuss the most eight common cyber threats, we're going to discuss in particular what they are? How the threat works and How to protect yourself
Cyber attacks are taking place all the time even as we speak the security of some organization big or small is being compromised, for example if you visit this site https://threatmap.checkpoint.com you can actually view all the cyber attacks that are actually happening right now. It's a pretty interesting site and actually gives you a scale of how many cyber attacks are actually happening all the time in the world
I think looking at all these types of cyber attacks, it's only necessary that we educate ourselves about all the types of cyber threats that we have. So the following are eight cyber threats that we are going to be discussing today:
1. Malware
Firstly, we're going to start with malware so malware is an all-encompassing term for a variety of cyber attacks, including Trojans, viruses and worms. Malware is simply defined as code with malicious intent that typically steals data or destroy something on the computer. The way malware goes about doing its damage can be helpful in categorizing what kind of malware you are dealing with. Let's us discuss the types of malware one after the other.
Viruses
Viruses like their biological namesakes viruses attach themselves to clean files and infect other clean files and they can spread uncontrollably damaging a system's core functionality and deleting or corrupting files. They usually appear as executable files that you might have downloaded from the internet.
Trojans
This kind of malware disguises itself as legitimate software or is included in legitimate software that can be tampered with, it tends to act discreetly and creates backdoors in your security to let other malware sin,
Worms
Worms infect entire networks of devices either local or across the internet by using the network's interfaces it uses each consecutive infected machine to infect more.
Botnets
Botnets are networks of infected computers that are made to work together under the controller of an attacker.
So basically you can encounter malware if you have some OS vulnerabilities or if you download some legitimate software from somewhere or you have some other email attachment that was compromised with.
Solutions to Malware
So how do you remove malware or how exactly do you fight against it? Well each form of malware has its own way of infecting and damaging computers and data and so each one requires a different malware removal method.
The best way to prevent malware is to avoid clicking on links or downloading attachments from unknown senders and this is sometimes done by deploying a robust and updated firewall which prevents the transfer of large data files over the network, and weed out attachments that may contain malware it's also important to make sure your computer's operating system whether it be Windows, Mac OS, Linux, uses the most up to date security updates and software programmers update programs frequently to address any holes or weak points, and it's important to install all these updates as well as to decrease your own system weaknesses
2. Phishing
So next up on our list of cyber threats we have phishing. So what exactly is phishing? Well often posing as a request for data from a trusted third party, phishing attacks are sent via email and ask users to click on a link and enter their personal data. Phishing emails have gotten much more sophisticated in recent years and making it difficult for some people to discern a legitimate request for information from a false one. Now phishing emails often fall into the same category as spam, but are way more harmful than just a simple ad. So how exactly does phishing work? Well, most people associate phishing with email message that spoof or mimic bank, credit card companies, or other businesses like Amazon, eBay and Facebook. These messages look authentic and attempt to get victims to reveal their personal information. But email messages are only one small piece of a phishing scam. From beginning to end, the process involves five steps.
Phishing Step by Step
The first step is planning the Phisher must decide which business to target and determine how to get email addresses for the customers of that business. Then they must go through the setup phase once they know which business to spoof and who their victims are phishers create methods for delivering the messages and collecting the data. Then they have to execute the attack and this is the step most people are familiar with that is the Phisher send the phony message that appears to be from a reputable source. After that the Fisher records the information the victims enter into the web page or pop-up windows. And in the last step, which is basically identity theft and fraud the Phishers use the information they've gathered to make illegal purchases or otherwise commit fraud, and as many as a fourth of the victims never fully recover.
Solutions to Phishing
So how exactly can you be actually preventing yourself from getting phished? Well, the only thing that you can do is being aware of how phishing emails actually work. So first of all, a phishing email has some very specific properties.
Phishing email properties include something like a very generalized way of addressing someone like dear client, some spelling and or grammatical errors and the message will not be actually from a very reputable source.
How Exactly Phishing Works?
Let me give you guys a quick explanation on how fishing actually works from the perspective of an attacker.
Assuming I wants to phish people's Facebook login credentials. So first of all, I have created a phishing website for harvesting Facebook credentials. I simply just took the source code of Facebook login page and pasted it and then made a back end code in PHP, which makes a log file of all the Facebook passwords that get actually entered onto the my phishing page. Now, I will send you an email address if i want to hack your Facebook account "Dear Client, we have strong reasons to believe that your credentials may have been compromised and might have been used by someone else. We have locked your Facebook account. Please click here to unlock, sincerely, Facebook associate team." . So when you open it, it looks pretty legit. It should look legit. If you actually click here, you will be redirected to a nice looking Facebook page, which is exactly how Facebook looks like when you're logging in, but actually its my Facebook phishing website. Now, when you try to login to your Facebook account on that page with your login credentials, once you click login, all that the back end code that I've written in PHP will do is that it's going to take all the parameters that you have entered into this website, i.e your Facebook email address and the password and just generate a log file about it and later redirect you to original Facebook login page. The log file generated by the backend will store your login credentials for me to use. You enter an email address and you're entering the email address on a phishing website and then it just redirects you to the original site. But by this time you've already compromised your credentials. So always be careful when dealing with such emails.
So this is how exactly pishing works, but this is explained only for the sake of awareness. Its absolutely illegal to practice it.
3. Password Attack
Jumping to our next type of cyber attacks we're going to discuss, password attacks. An attempt to obtain or decrypt a user's password for illegal use is exactly what a password attack is. Hackers can use cracking programs, dictionary attacks. and password sniffers for password attacks
Password cracking refers to various measures used to discover computer passwords. This is usually accomplished by recovering passwords from data stored in or transported from a computer system, password cracking is done by repeatedly guessing the password usually through a computer algorithm in which the computer tries numerous combinations until the password is successfully discovered.
Now password attacks can be done for several reasons, but the most malicious reason is in order to gain unauthorized access to a computer with the computer's owners awareness not being in place. Now this results in cybercrime such as stealing passwords for the purpose of accessing bank information and other secret data.
There are three common methods used to break into a password protected system. The first is a brute force attack where a hacker uses a computer program or script to try to log in with possible password combinations, usually starting with the easiest to guess password.
The next is dictionary attacks, a hacker uses a program or script to try to log in by cycling through the combinations of common words. In contrast with brute force attacks where a large proportion key space is searched systematically a dictionary attack tries only those possibilities which are most likely to succeed, typically derived from a list of words, e.g dictionary. Generally dictionary attacks succeed because most people have a tendency to choose passwords which are short or such as single words found in the dictionaries or simple easy predicted variations on words such as appending a digit or so.
Now the last kind of password attacks are used by key logger attacks, in this type, hacker uses a program to track all of the users keystrokes. So at the end of the day everything the user has typed including the login IDs and passwords have been recorded. A key logger attack is different from a brute force or dictionary attack in many ways, the least of which the key logging program used as a malware that must first make it onto the user's device. And the key logger attacks are also different because stronger passwords don't provide much protection against them which is one reason that multi-factor authentication is becoming a must-have for all businesses and organizations.
Now the only way to stop yourself from getting killed in the whole password attack conundrum is by actually practicing the best practices that are being discussed in the whole industry about passwords.
So basically you should update your password regularly. You should use alpha numerics in your password and you should never use words that are actually in the dictionary.
It's always advisable to use garbage words that makes no sense for passwords as they just increase your security.
4. DDOS Attack
So moving on we're going to discuss DDoS attacks. So what exactly is a DDoS or a dose attack? Well, first of all, it stands for distributed denial of service and a dose attack focuses on disrupting the service to a network. As the name suggests, attackers send high volume of data of traffic through the network until the network becomes overloaded and can no longer function. So there are a few different ways attackers can achieve dose attack. But the most common is the distributed denial of service attack. This involves the attacker using multiple computers to send the traffic or data that will overload the system, in many instances a person may not even realize that his or her computer has been hijacked and is contributing to the dose attack. Now disrupting services can have serious consequences relating to security and online access many instances of large-scale dose attacks have been implemented as a single sign of protests towards governments or individuals and have led to severe punishment including major jail time.
Solutions to DDOS Attack
So how can you prevent dose attacks against yourself? Well firstly unless your company is huge. It's rare that you would be even targeted by an outside group or attackers for a dose attack, your site or network could still fall victim to one. However, if another organization on your network is targeted now the best way to prevent an additional breach is to keep your system as secure as possible with regular software updates online security monitoring and monitoring of your data flow to identify any unusual or threatening spikes in traffic before they become a problem.
Dose attacks can also be perpetrated by simply cutting a table or dislodging a plug that connects your website server to the internet.
So due diligence in physically monitoring your connections is recommended as well.
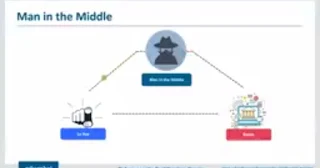
5. Man in the Middle Attacks
Next up on our list is man-in-the-middle attacks. This is done by impersonating the endpoints in an online information exchange. The man-in-the-middle attack can obtain information from the end user and the entity he or she is communicating with, for example, if you are banking online the man in the middle would communicate with you by impersonating your bank and communicate with the bank by impersonating you. The man in the middle would then receive all of the information transferred between both parties which could include sensitive data such as bank accounts and personal information.
How Does Man in the Middle Attack Work?
So how does it exactly work? Normally an attacker using MITM gains access through a non-incredible and encrypted wireless access point, which is basically one that doesn't use wap, wpa or any of the other security measures then they would have to access all the information being transferred between both parties by actually spoofing something called address resolution protocol. That is the protocol that is used when you are actually connecting to your Gateway from your computer.
Solutions to MITM Attacks
So how can you exactly prevent MITM attacks from happening against you? Firstly you have to use an encrypted wap that is an encrypted wireless access point.
Next, you should always check the security of your connection because when somebody is actually trying to compromise your security, he will try to actually strip down the SC DPS or SSDs that is being injected in the website, which is basically the security protocols.
So if something like this SC DPS is not appearing in your website, you're on an insecure website where your credentials or your information can be compromise.
The last and final measure that you can actually use is by investing in a virtual private network, which spoofs your entire IP and you can just browse the internet with perfect comfort.
6. Drive-by Downloads
Next up on our list is drive-by downloads. Gone are the days where you had to click to accept a download or install a software update in order to become infected. Now just opening a compromised web page could allow dangerous code to install on your device. You just need to visit or drive by a web page without stopping or to click accept any software and the malicious code can download in the background to your device.
A drive-by download refers to the unintentional download of a virus or malicious software onto your computer or mobile device. A drive-by download will usually take advantage or exploit a browser or app or operating system that is out of date and has security flaws. This initial code that is downloaded is often very small, and since his job is often simply to contact another computer where it can pull down the rest of the code onto your smartphone tablet or other computers. Often a web page will contain several different types of malicious code in hopes that one of them will match a weakness on your computer.
How Does Drive-by Download Works
So how does this exactly work? Well first you visit the site and during the three-way handshake connection of the TCP IP protocol a backend script is triggered as soon as the connection is made while the last AC key packet is sent, a download is also triggered and the malware is basically injected into your system.
Solutions to Drive-by Download
Now the best advice I can share about avoiding drive-by downloads is to avoid visiting websites that could be considered dangerous or malicious. This includes adult content, file sharing websites or anything that offers you a free trip to the Bahamas.
Now some other tips to stay protected include keep your internet browser and operating system up to date, use a safe search protocol that warns you when to navigate to a malicious site and use comprehensive security software on all your devices, like McAfee all access and keeping it up to date.
7. Malvertising
Next up is mal-advertising or malvertising. So malvertising is the name we in the security industry give to criminally controlled advertisements, which intentionally infect people and businesses. These can be any ad on any site often ones which you use as a part of your everyday internet usage and it is a growing problem as is evident by a recent US Senate report and the establishment of bodies like trust in ads whilst the technology being used in the background is very advanced the weight presents to the person being infected is simple to all intents and purposes. The advertisement looks the same as any other but has been placed by criminal. Without your knowledge a tiny piece of code hidden deep in the advertisement is making your computer go to the criminal servers these and catalog details about your computer and its location before choosing which piece of malware to send you and this doesn't need a new browser window and you won't know about it. So basically you're redirected to some criminal server. The malware injection takes place and voila you're infected. It's a pretty dangerous thing to be in.
Solutions to Malvertising
So how exactly can you stop malvertising? Well, first of all, you need to use an ad blocker which is a very must in this day and age. You can have ad blocker extensions installed on your browser whether it be Chrome Safari or Mozilla. Also regular software updates of your browser and other softwares that work peripheral to your browser always helped
Next, is some common sense, any advertisement that is about a lottery that's offering you free money is probably going to scam you and inject the malware, so never click on those ads.
8. Rogue Software
The last kind of cyber attacks, we are going to discover today and discuss about is rogue software. So rogue security software is a form of malicious software and internet fraud that misleads users into believing that there is a virus on their computer and manipulates them into paying money for a fake malware removal tool.
It is a form of scareware that manipulates users through fear and a form of ransomware. Rogue security software has been a serious security threat in desktop computing since 2008.
How Does Rogue Software Works
So now how does the rogue security software book these camps manipulating users into download the program through a variety of techniques. Some of these methods include ads offering free or trial versions of security programs often pricey upgrades or encouraging the purchase of the deluxe versions.
Then also pop-ups warning that your computer is infected with a virus which encourages you to clean it by clicking on the program.
Then manipulated SEO rankings that put infected website as the top hits when you search these links then redirected to a landing page that claims your machine is infected and encourages you a free trial of the rogue security program.
Now once the scareware is installed it can steal all your information, slow your computer, corrupt your files, disable updates for legitimate antivirus softwares or even prevent you from visiting legitimate security software vendor sites.
Solutions to Rogue Software
Well, talking about prevention, the best defense is a good offense and in this case an updated firewall makes sure that you have a working one in your office that protects you and your employees from these type of attacks. It is also a good idea to install a trusted antivirus or antispy software program that can detect threats like these and also a general level of distrust on the internet and not actually believing anything right away is the way to go.
Okay guys, so that is it about all the eight different types of cyber threats and how they actually work and how you could prevent them. Goodbye, I hope you have enjoyed reading this post. Please be kind enough to share it and you can comment any of your doubts and queries and we will reply them at the earliest do look out for more posts by visiting this website regularly. Happy learning.





Comments
Post a Comment